For too long, cybersecurity compliance has felt like a periodic scramble — a complex, manual process triggered only
AI cyber threats are on the rise, and traditional security measures are no longer enough. To combat these
AI is transforming cybersecurity, and not always for the better. As businesses become more dependent on digital tools,
AI technology is a double-edged sword. While it empowers businesses with innovative tools, it also equips cybercriminals with
Microsoft Word is a fundamental tool for businesses, enabling the creation of professional documents, reports, and correspondence. While
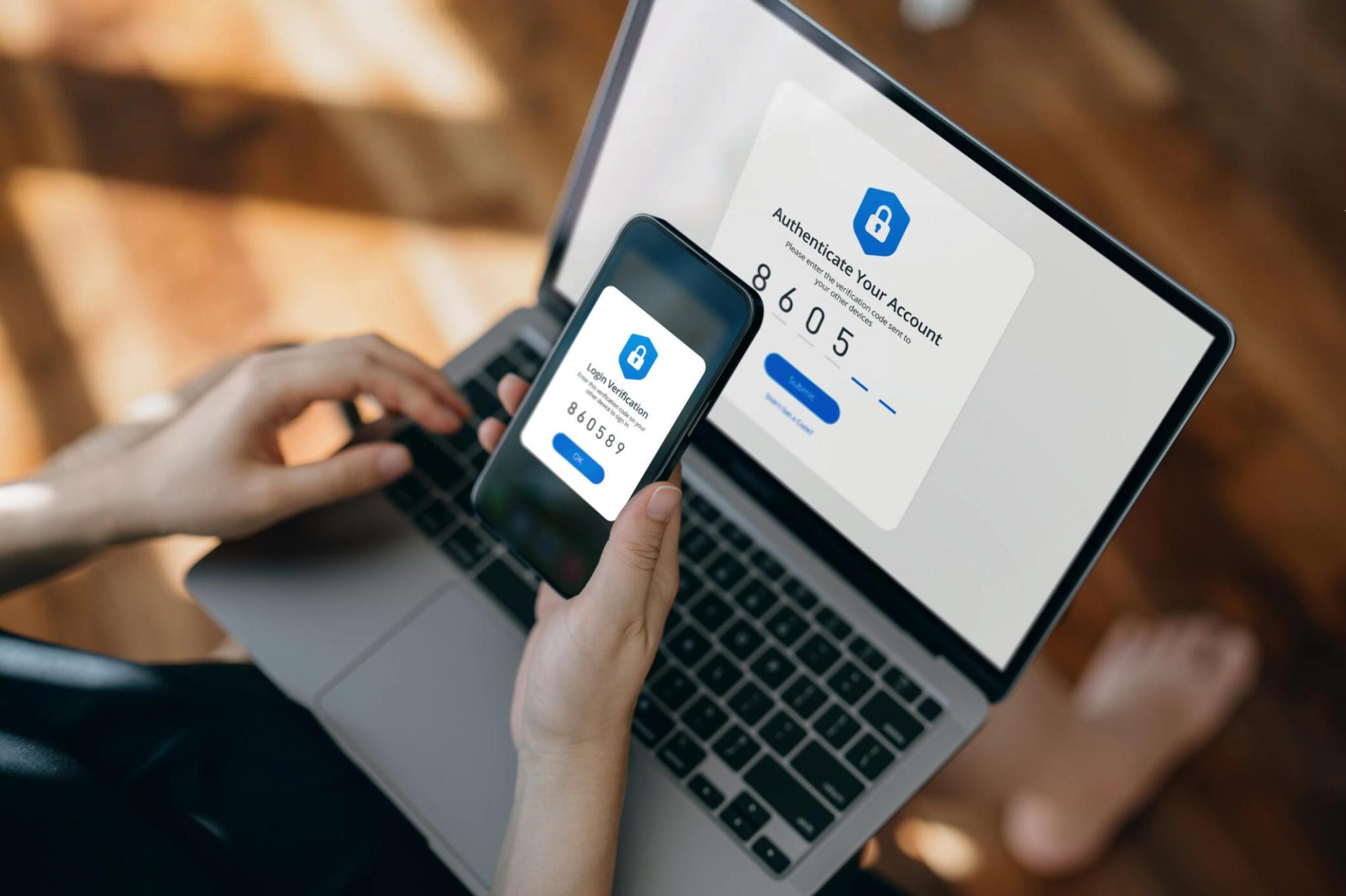
Protecting this data is crucial, and one of the most effective ways to ensure its safety is through
Disaster recovery is an essential aspect of any business continuity plan, ensuring that operations can quickly resume following
In today’s fast-paced business environment, effective use of technology is key to maintaining productivity and staying ahead of
The cyber security landscape in Australia is growing increasingly perilous, with a marked surge in phishing attacks, email
In an era where technology is rapidly evolving, the importance of robust cyber security measures cannot be overstated.
In today’s digital age, staying informed about cyber security threats is crucial for businesses of all sizes. As
Check our latest articles