Essential Eight Assessment
Developed as an evolution of the ASD’s Top Four recommendations, the Essential Eight serves as a baseline to strengthen your organisation’s cybersecurity defences.
Essential Eight Assessment for Enhanced Cyber Security Protection
AI-driven cyber threats are becoming increasingly sophisticated, targeting businesses of all sizes. Is your organisation prepared? Genisys offers a comprehensive Essential 8 Assessment tailored to identify vulnerabilities, implement robust safeguards, and protect your business against emerging cyber threats.
Why the Essential 8 Framework is Vital
The Essential Eight is a framework developed by the Australian Cyber Security Centre (ACSC) to help organisations mitigate cyber threats. This assessment evaluates an organisation’s cybersecurity maturity levels based on the Essential Eight, enabling businesses to identify vulnerabilities, address risks, and enhance their overall cyber resilience. These strategies, based on the ACSC’s Strategies to Mitigate Cyber Security Incidents, provide a prescribed list of technical measures designed to mitigate threats to your business.
Unlock these benefits conducting the Essential Eight Assessment






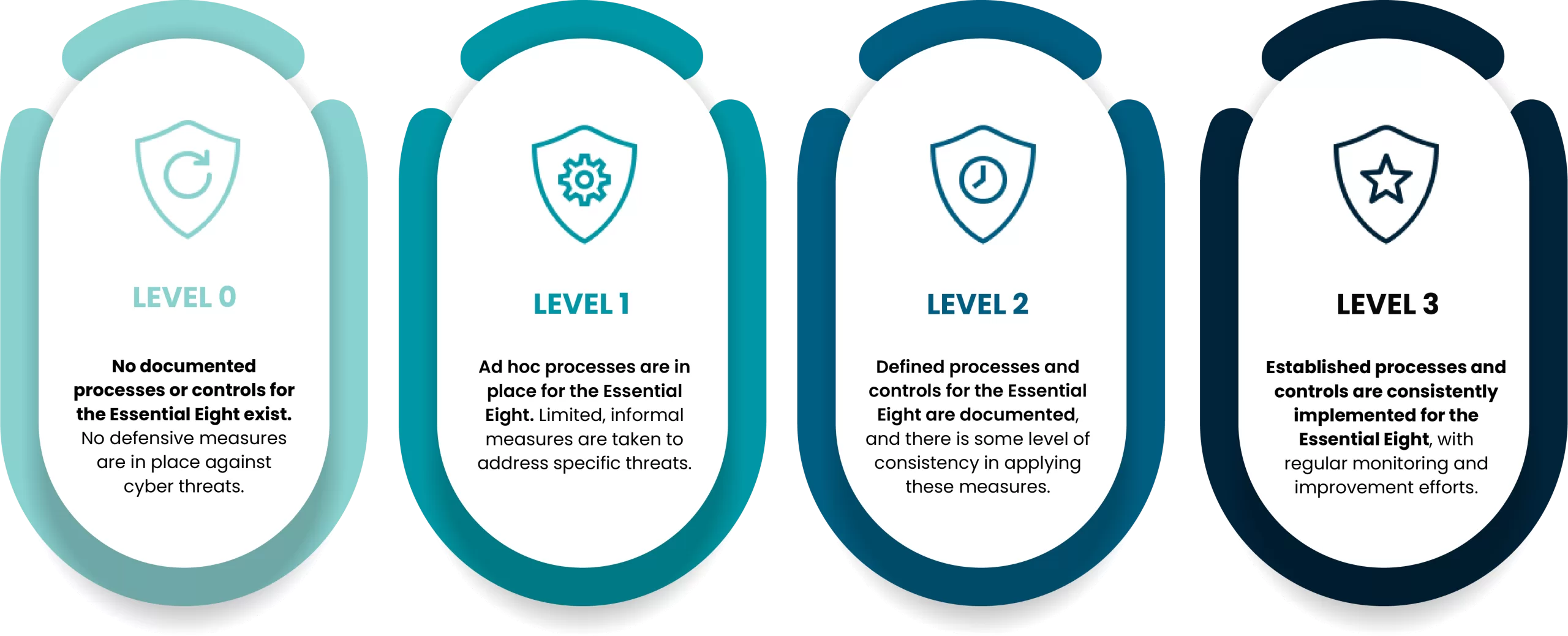
Understanding the Essential 8 Maturity Levels
The Essential 8 Maturity levels, as outlined by the ACSC, are designed to measure an organisation’s cybersecurity posture and capability to effectively implement the Essential 8 strategies. The levels include:
Why Choose Genisys
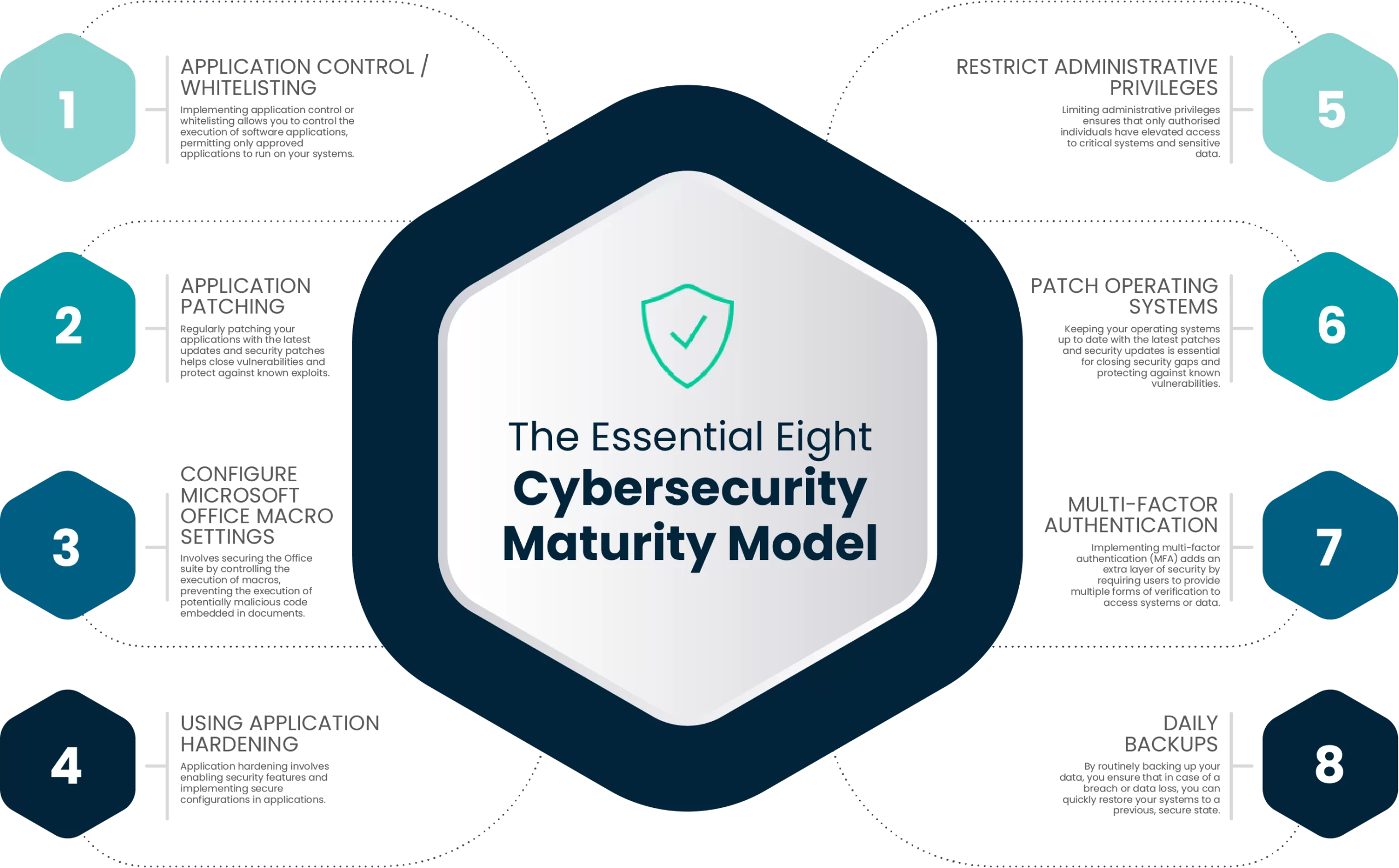
Exploring the Essential Eight Strategies
By adopting these Essential Eight strategies, organisations can establish a robust foundation to protect against a wide range of cyber threats, including malware infections, unauthorised access attempts, and data breaches.
Our solutions
Ready to take control of your business’s cybersecurity?
Try our Free Essential 8 Maturity Assessment Survey today and gain valuable insights into how your current security measures up. Get a comprehensive understanding of your organisation’s security position and identify areas that might need attention.








